
Report on Controls at a Service Organization Relevant to Security, Availability, Processing Integrity, Confidentiality or Privacy
These reports are intended to meet the needs of a broad range of users that need detailed information and assurance about the controls at a service organization relevant to security, availability, and processing integrity of the systems the service organization uses to process users’ data and the confidentiality and privacy of the information processed by these systems. These reports can play an important role in:
- Oversight of the organization
- Vendor management programs
- Internal corporate governance and risk management processes
- Regulatory oversight
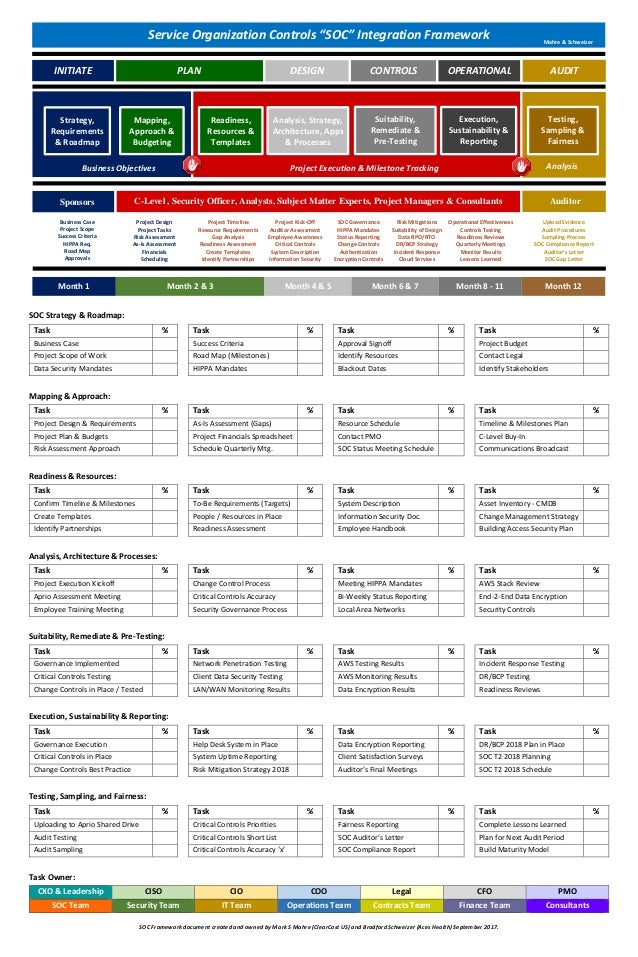
Soc 2 Controls List Excel Spreadsheets
SOC 2 Report is based upon the Trust Services Principles, with the ability to test and report on the design and operating effectiveness of a service organization’s controls. The SOC 2 report focuses on a business’s non-financial reporting controls as they relate to security, availability, processing integrity, confidentiality and privacy of. SOC 2 for Cloud CSA STAR Attestation The SOC 2+ Framework allows an SOC 2 to report on any additional controls over and above the trust services criteria controls for security, availability, confidentiality, processing integrity and privacy. Determining which of the criteria to include in the scope of a SOC 2 examination is a key step in the SOC 2 planning process. A service organization should do their homework and know a little about the available criteria and if they apply to their services and system. SOC stands for “System and Organization Controls” and is the agreed upon procedures of controls set by the American Institute of Certified Public Accountants (AICPA). These defined controls are a series of standards designed to help measure how well a given service organization conducts and regulates its information. See more: what is soc 2, what does soc 2 stand for, soc 2 type 2 audit checklist, what is soc 2 compliance, soc 2 report example, soc 2 controls list, soc 2 wiki, soc 2 compliance checklist, visual basic support, odin diet visual basic support, read level microphone visual basic, school level project visual basic hospital management source code.
Similar to a SOC 1 report, there are two types of reports: A type 2 report on management’s description of a service organization’s system and the suitability of the design and operating effectiveness of controls; and a type 1 report on management’s description of a service organization’s system and the suitability of the design of controls. Use of these reports are restricted.
The American Institute of Certified Public Accountants (AICPA) System and Organization Controls (SOC) is a suite of service offerings CPAs may administer in connection with system-level controls of a service organization or entity-level controls of other organizations. SOC provides internal control reports on the services provided by a service organization. Free Download of SOC2 Trust Principles and Security Controls as a flat-file XLS CVS file. Email for custom controls mapping to your.
Developed to ensure the privacy and security of customer data, SOC 2 compliance is critical for all enterprises that process, store, or transmit this data.Although SOC 2 attestation is completely voluntary, not having it can be a huge red flag, telling potential customers and clients that their secrets aren’t safe with you or your vendors.The good news is, the is flexible. Using the framework requirements as a guide, your enterprise can write internal controls that fit your unique situation and needs. But how can you know if you’re doing SOC 2 right? Over time, IT services became more central to business, and more organizations opted to outsource their technology functions to third-party service providers such as Software-as-a-Service (SaaS) vendors.But SAS 70 was designed for financial audits, not for assessing data security and privacy controls. So in 2011 AICPA issued the Statement on Standards for Attestation Engagements No. 16 (SSAE 16).
Often, organizations will designate a team to oversee and coordinate SOC 2 compliance efforts. The job titles of these positions may include:. Executive sponsor. This may be your:. Chief Technology Officer (CTO). Chief Information Officer (CIO).
Chief Security Officer (CSO). Chief Information Security Officer (CISO). Chief Risk Officer (CRO). SOC 2 project manager.
Author. Legal. IT. Information security. Risk officer/risk manager. Compliance officer/compliance manager. IT auditor.
Consultant. How about now? Because, chances are, your competitors are already SOC 2 certified.Every that handles customer or client data, from scrappy startups to multinational corporations, should be compliant with this increasingly important framework.
But SOC 2 certification is no quick-and-easy deal. It requires teamwork, advance planning, coordination, internal audits, and more.In the meantime, your risk of data breaches is higher than it needs to be. Opportunities for business might be passing you by.Even if you already have your SOC 1 attestation, you’ll still need SOC 2. Because, while SOC 1 deals with financial reporting, SOC 2 generates internal control reports around those five trust principles: data security, privacy, processing integrity, confidentiality, and availability.A SOC 2 report can take nine months or even a year to complete, especially if you’re using spreadsheets to track your progress.Or: ZenGRC can help you SOC 2 compliance in a fraction of the time.
Contact one of our experts today to find out how. Getting to can be a long and arduous process, with a lot of moving parts, policies, and procedures to align. A methodical approach works best. We suggest:1.Appoint your SOC 2 team members. Can help you decide who should be on this important team.2.Set your goals. Do you want a Type 1 report, or Type 2? Do you want SOC 2 attestation for a single product or service, or your entire organization?3.Determine your scope.
Which of SOC 2’s five Trust Services Categories apply to your organization? Which of SOC 2’s 61 Trust Services Criteria apply?4.Organize your materials. For each Trust Services Criterion you’ve chosen in step 2, determine which controls apply, evaluate whether they are effective, resolve any gaps, and gather the documents you need as proof.
Organize evidence around the five trust categories: security, availability, confidentiality, processing integrity, and privacy of customer data.5.Self-audit. The point here is to do your work in advance. If you wait until the last moment to pull together documentation, establish an audit trail, and identify and fill gaps, you may face audit findings and a denial of attestation—more harmful than if you had never sought certification in the first place.6.Monitor yourself. Setting up security monitoring and alerts can help keep you from falling out of compliance before the SOC 2 auditor arrives.7.Get a SOC 2 audit. The AICPA stipulates that only an independent Certified Public Accountant is qualified to perform your SOC 2 audit. Your auditor may engage an independent, experienced SOC 2 specialist to assist, if necessary. Like cybersecurity risk, SOC 2 quite frequently: the AICPA issued updates in 2016 and 2017.
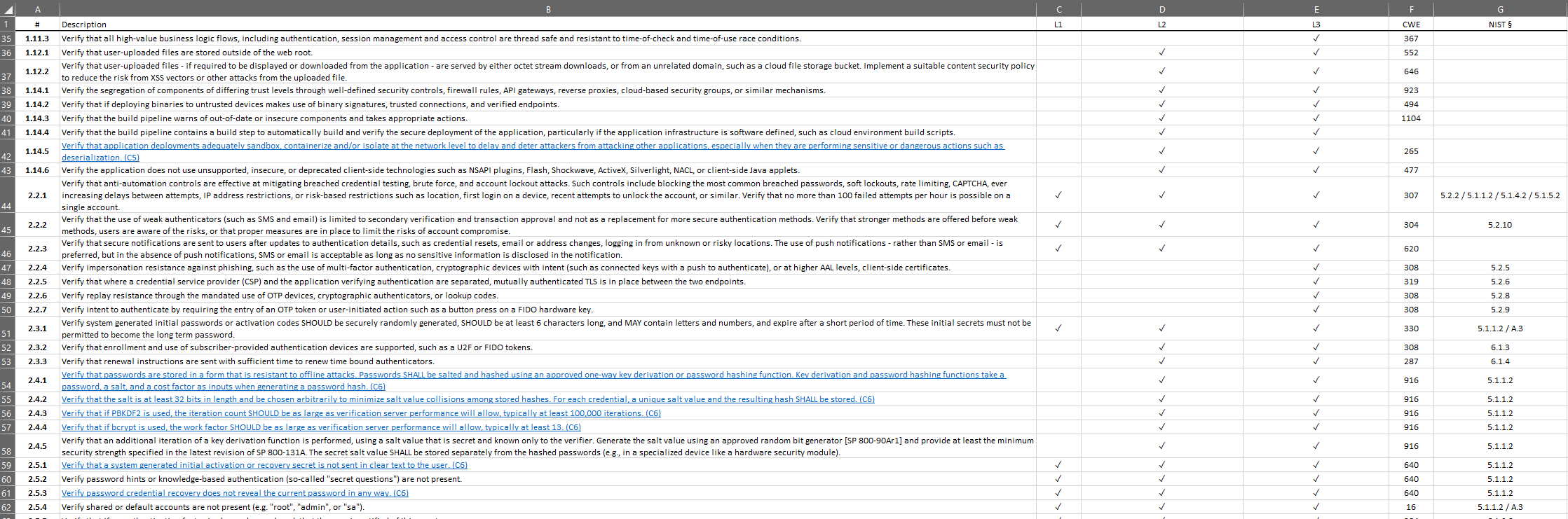
Soc 2 Controls List Excel Spreadsheet

This head-snapping pace can make maintaining your SOC 2 compliance a challenge, but we’re here to help.The latest revisions, effective for review periods ending after Dec. 2018, represent the most comprehensive SOC 2 updates since the framework’s creation. They include:.
Alignment of the SOC 2 Trust Services Principles and Criteria with the Committee of Sponsoring Organizations of the Treadway Commission (COSO 2013) framework, the world’s most widely used internal controls framework. The AICPA made this important change to help organizations use COSO to audit their internal controls. New rules for file integrity monitoring and vendor risk management. Requirements for setting up a fraud whistleblower policyThe 2017 update established SOC 2+, a new type of report that allows you to address criteria from other frameworks including,27001, Cloud Security Alliance (CSA),800-53 and.Look for more changes in SOC 2 as the cybersecurity and risk landscape continues to shift. A SOC 2 assessment works much like any other. The independent Certified Public Accountant or accounting firm you choose can help you:.Determine your, a critical first step in which you determine:. Which of the 5 SOC principles, now called Trust Services Categories, apply to your organization.
Which SOC report you need: Type 1 or Type 2. Most organizations choose Type 1, which considers SOC 2 compliance at a point in time, for their first SOC 2 audit, and Type 2, which examines compliance over a period of time, for subsequent audits.For each applicable Trust Services Category, the auditor will examine your controls, a process that includes evidence collection, to evaluate whether they are working as they should. Documents the auditor may examine include:. Organizational charts. Asset inventories.
Soc 2 Control Objectives
Onboarding and off-boarding processes. Change management processesIf the auditor finds problems or gaps, no worries: You’ll have an opportunity for remediation. Findings can drive up audit costs, however, so thorough preparation using a is your best bet for efficiency and ease. The key to SOC 2 readiness is preparation.
Before the auditor walks in your door, you should have checked off all the boxes on your checklist and have your supporting evidence on hand. Here’s how to prepare:. Establish your goals. What is the of your audit? Begin by establishing which of the SOC 2 Trust Service Categories and their 61 principles apply to your organization. Those categories, governing how your organization processes personal information, are:.
Security. Availability. Processing integrity. Confidentiality.
Privacy. Organize your materials—the documents and correspondence proving the effectiveness of your controls—in line with the Trust Services Categories and Principles you’ve deemed applicable. Conduct a self-audit. This step can save untold grief and cost down the road. If you can show the professional conducting your SOC 2 audit that you have remediated compliance issues or are in the process of doing so, your organization will be well on its way to achieving that coveted SOC 2 attestation.

Get help if you need it. Let’s face it: If SOC 2 certification were easy, everyone would have done it already. SOC 2 is a complex framework that changes frequently, and can be confusing—especially for organizations trying to manage compliance with Excel or other spreadsheets. ISO 27001 is another framework governing information security, and its standards are more rigorous than SOC 2's.
If your organization is already ISO 27001 certified, should you even bother withThe short answer is, “yes.” While the two standards have similarities, the are significant enough that many enterprises will want to show compliance with both.Developed by the International Organization for Standardization, ISO 27001 guides enterprises in establishing an information security management system (ISMS). Preparing for the audit typically takes about three years, and results in certification which then must be renewed annually.Governed by the AICPA, SOC 2 audits measure the effectiveness of existing security programs, and results not in certification but in a CPA’s “attestation” report.Which to pursue—and whether to strive for compliance with both—depends on a number of factors.

It’s safe to say, however, that if you are ISO 27001 certified, you probably are already in compliance with much of SOC 2. If you’re using Excel or other spreadsheets to track and manage your organization’s SOC 2 compliance, you’re working too hard. Juggling paperwork is time-consuming and confusing, and drives up SOC 2 certification/attestation costs.In today’s high-tech world, there’s an application or tool for pretty much everything. Productivity/organization, workflows, human resources onboarding, identity access management, risk management, and other tasks governed by SOC 2 controls can now be done efficiently and effectively using a variety of software types. Choosing the right software for your service organization can be a difficult task. How can you know which will work best with your compliance management program?The fact is, not all compliance platforms are created equal. For best results, choose a SOC 2 compliance tool with:.
Quick, easy deployment. User-friendly design. Easy internal audit capabilities. Vendor management tools. Continuous controls monitoring. Integration with your software and services stack.
At-a-glance compliance dashboards that include your other frameworkshas these features and more to move you into worry-free SOC 2 compliance and yearly renewals of your AICPA attestation—so your clients will breathe easily, too, knowing their customer data is as safe and secure as can be.

Comments are closed.